WordPress XML-RPC: What is Xmlrpc.php and DDoS Attack
Contents
Today our web servers, one in particular (web02), experienced a WordPress XML-RPC DDoS (distributed denial of service) attack designed to specifically target WordPress websites.
Our technicians quickly identified the attack, and implemented a solution to block the bot net of attacks to our servers, but this did cause websites to load slow (if at all) for approximate 2 hours.
What is WordPress XML-RPC?
XML-RPC, or XML Remote Procedure Call, allows remote interaction with WordPress sites, including the ability for remote updates to WordPress from other applications, including trackbacks and pingbacks, Jetpack (plugin)
What was the DDoS attack?
This attack targeted the XML-RPC feature of WordPress, where a collection (thousands) of other infected WordPress site (bots) targeted WordPress sites hosted with us.
The bots did this by generating a lot of HTTP GET and POST requests to the WordPress URL /xmlrpc.php, causing excessive server CPU and memory usage, essentially making the sites unresponsive, and not responding for legitimate users.
Solution to stop XML-RPC attacks
Once we identified the attack, we used the Fail2ban tool to identify any request to the URL “/xmlrpc.php”, and after 2 requests ban that IP address for up to 12 hours.
We can easily white-list specific IP addresses to get around this blanket ban, should clients need remote access to WordPress XML-RPC, so please contact us if this is required.
The fail2ban filter we used was: (file /etc/fail2ban/filter.d/wordpress-xmlrpc.conf)
[Definition]
failregex = ^<HOST> .* "(GET|POST) .*xmlrpc.php
ignoreregex =
And the rule to enable this filter was: (file /etc/fail2ban/jail.local):
[wordpress-xmlrpc]
enabled = true
port = http,https
filter = wordpress-xmlrpc
action = iptables-multiport[name=wordpress-xmlrpc, port="http,https", protocol=tcp]
logpath = /var/log/ispconfig/httpd/*/access.log
maxretry = 1
findtime = 43200 ; 12 hours
bantime = 43200 ; 12 hours
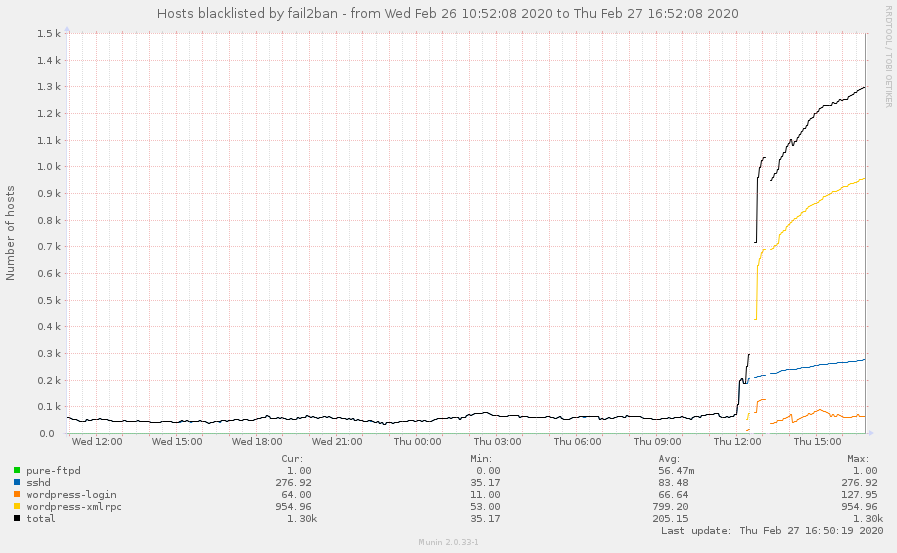
The graph below was taken from our web02 server, showing the number of IP addresses blocked via fail2ban for this xml-rpc attack, starting just before midday.
So far the web02 server has blocked over 1200 individual IP addresses, and all our other servers combined this jumps to over 5000 IP addresses across 16 servers.
Do you still need XML-RPC functionality in WordPress ?
If you still require XML-RPC functionality in WordPress to remotely interact with your site, there are multiple options:
- We can white-list (allow) the IP address of your remote service that needs to interact with your WordPress xml-rpc.php URL.
Please contact us with this request, with your website URL, remote IP address that requires access, and use case for this. - Use the WordPress REST API plugin as an alternative for remote updating and features: https://wordpress.org/plugins/rest-api/
- In time we expect the features of XML-RPC to become integrated directly into the WordPress core via the new WordPress API, to replace the old xmlrpc.php URL functionality

0 comment